Overview
State-of-the-art technologies are now widely used to enhance manufacturing, banking, and virtually any business, bringing revolutionary innovations to the information sphere. Web 3.0 introduces the concept of decentralization as the foundation of the modern internet. The majority of computer systems and networks require security and decentralization to meet their needs for privacy.
Industry
The decentralization solution is a distributed ledger technology called Blockchain.
Blockchain can be thought of as a massive database that exists eternally, keeping its history safe from interference and changes. Blockchain provides a foundation for decentralized web applications and various types of services.
Blockchain enables users to create P2P transactions, increase trust between network participants, perform business logic, and solve practical consensus tasks within the network.
Company
Opporty is a research project that creates innovations for B2B transactions, leveraging Blockchain for the independent evaluation of companies, efficient dispute resolution, use of smart contracts, and purchasing and selling of services without intermediaries.
Opporty’s Team includes:
- Cybersecurity and cryptology specialists.
- DAPP interfaces developers.
- DevOPS specialists for organizing and setup of the infrastructure for blockchain projects.
- Microservice architecture developers.
Background
Blockchain technology has huge potential. Its reliability and scalability far exceed existing methods for operating and managing businesses.
It is impossible to ignore Blockchain’s capability for accurate tracking and recording of data, executing faster and safer transactions.
As much as any new technology, Blockchain has met with a variety of issues and challenges, but has resolved them one by one, becoming an integral part of modern business operations.
Although we cannot predict when Blockchain will become a must-have technology for every B2B company, it is rapidly picking up steam, with no sign of slowing down. Meanwhile, progressive B2B companies are already leveraging Blockchain’s enhanced security, efficiency and trustworthiness, keeping a step ahead of their competitors.
Blockchain offers new solutions that outperform traditional methods of doing business:
1. Preventing Unnecessary Expenses.
Say goodbye to missed transactions, banking software malfunctions, human errors, and uncoordinated transfers.
Once transaction data enters the Blockchain, it is immediately coded into the main distributed ledger system. A safe validation mechanism is also performed.
The network stores a great amount of identical information, which means that Blockchain does not have a controller or a single point of failure.
2. Transparent Transactions.
It is said that B2B companies gain secure and transparent transactions when they choose Blockchain, but what exactly does that mean?
Implementing relevant Blockchain practices means not having to worry about manipulation and data tampering. The network performs as a self-monitoring system, continually checking its digital values.
Each transaction is confirmed within a 10-minute interval. A single block is a group of transactions.
Transparency data is implemented into the network and is made public. The information itself cannot be damaged or changed.
3. Digitalization For Real Products.
Blockchain technology is eminently suitable for recording the history of real goods and products.
For example, each car has its own digital representation on the Blockchain. No one can manipulate the information, thanks to the network’s security. Meanwhile, you can use the records to maintain the car’s daybook. Moreover, you can check the product’s authenticity, the number of previous owners and their names, and other information at any time.
4. Smart Contracts.
Smart contracts are computer protocols that are set individually for a particular transaction. A smart contract includes a set of business rules and an automatic execution of the contract’s terms.
Smart contracts enhance security, reduce hacking risks, optimize transactions, and eliminate the need for intermediaries.
5. Fast and Safe Payments.
If you use digital payment services, there is a good chance that these services are not decentralized. The majority of digital payment services are still centralized.
This means that each transaction you launch has to be approved by an external party. This is why some transfers can take several days or even weeks.
Transactions via Blockchain can be much, much faster.
Smart contracts accelerate transactions for B2B payments. Blockchain technology removes external entities, focusing on peer-to-peer transactions, reducing the cost and time for handling each transaction.
Your transfers no longer take weeks to pass through third parties. Instead, they are quickly approved via the Blockchain system.
Advantages:
- Fast transaction speeds accelerate the entire supply chain, satisfying clients’ requirements.
- Optimized distribution and logistics.
- Cost savings on third-party services.
Automatization means faster payments can be sent to employees. They no longer need to wait the traditional two weeks after completing a job. Employees can be paid every week or every day.
Opporty’s goal is to outpace traditional payment systems in speed, accessibility and reliability.
The Challenge
Execution of smart contracts and rapid application performance within a distributed database can be made possible only after fulfilling the conditions of high scalability.
Modern decentralized Blockchain solutions have some downsides, and scalability is the major one. Ethereum handles about 20 transactions per second, which is an unsatisfactory number for today’s financial realities. Nevertheless, it offers the highest protection from hacking and network malfunction. Other cryptocurrencies and blockchain-based systems do not have such a high degree of decentralization, which reduces credibility within the network.
The Scalability Trilemma
The Scalability Trilemma consists of three elements:
- Decentralization,
- Security,
- Scalability.
Decentralization in the Trilemma
Decentralization, as the word suggests, refers to the degree of diversification in ownership of an activity within the Blockchain, and diversification in creating blocks and generating new ledger records. Ethereum is very decentralized; Eos is partially decentralized; Facebook is not at all decentralized. All blockchains are decentralized to varying degrees.
To simplify things, let’s start with the most centralized types of organizations. Typically, these organizations use simple databases instead of Blockchain. Such organizations are usually run by managers or administrators. All transactions can be terminated manually.
Complete decentralization allows users to take part in the network creation.
Users collectively have the ability to use their stakes to vote, to utilize services on the platform, and to benefit financially. Obviously, while all blockchain users can stake their tokens to vote, their degree of influence varies. In proof-of-stake (PoS) protocols, the influence of a single user is proportional to the number of tokens the user owns. In delegated proof-of-stake (DPoS) protocols, the number of tokens affects a user’s right to vote for another user who already participates in the block creation.
The crucial element of decentralization is that the majority of value accrues to the community that participates in the blockchain creation. There is no intermediate management team reaping benefits from those who generate the network’s structure. Most crypto projects are owned by their contributors or users, rather than by founders. This is obviously a more appealing proposition for those who are not founders.
Pros And Cons Of Decentralized Protocols
- The more decentralized the system, the stronger the security that can be achieved. There is no single point of failure or hack. However, some hacking methods exist, even for the most decentralized systems
- Decentralization aims to bring power back to the community. The influence of each community member must be spread evenly.
- The downside is that there is no central moderator, something that can be useful in certain cases, such as moderating messages on social media.
- Decentralization in classic PoW protocols requires vast amounts of energy and electricity to be spent in vain.
- It is impossible to shut down a growing decentralized blockchain. If a destructive scenario were to arise, this would cause a problem.
Security in the Trilemma
Security refers to a blockchain’s level of defensibility against attacks from external sources. It is a measure of the system’s immutability to change. For the majority of blockchains, there are many potential threats to security. Decentralization and security go hand in hand. In many cases, the more nodes there are, the less reliant the network is on a centralized party, and therefore the lower the risk of having a central point of failure. However, there are a number of other attack vectors that pose risks to decentralized networks, including:
> 50% Attack – an entity owning more than 50% of the total number of unpaid tokens effectively owns the network.
> Sybil Attack – a user can generate multiple identities in the system to effectively control a significant stake in ownership and/or decision-making of the network.
> DDoS – Distributed Denial of Service Attack occurs when there is intent to disrupt traffic in a network by flooding the network with malicious transactions.
> Collusion Attack – one or more entities (or nodes) agree to collude together to perform some malicious operation within the network
Pros And Cons Of Advanced Security
- The major benefit of advanced security is that the blockchain is less vulnerable to attacks, making it perfect for applications that require high-grade security and deal with confidential data. Everything connected with financial services would likely require the highest degree of security.
- There are no downsides in maintaining robust security, but some minor issues do exist. Many secure blockchain networks utilize PoW protocols . Consensus requires solving of complex hash puzzles to block production, but more importantly, these protocols use up an immense amount of computing power and energy. Consequently, this reduces throughput and increases network latency, a strong deterrent for many potential users.
Scalability in the Trilemma
The degree of scalability is important because it dictates the eventual capacity of any network. In other words, it determines the upper limit on how large a network can grow. It is perhaps the most important question to think about when evaluating a network — how many users can this network sustain? Bitcoin currently has between 2.9 to 5.8 million wallet holders; Eos has a few thousand.
Scalability and decentralization can coexist, but security risks become greater. Developers tend to choose the platform that meets their needs in the best way, and users tend to choose the platforms that perform in the most suitable way. Some users may be willing to sacrifice security for scalability; others, scalability for security.
Pros And Cons Of Scalability
- Scalability ensures that the application runs quickly and that it can support a high volume of transactions. This is especially useful for audio/video streaming sites, gaming, and social media.
- The application is less likely to break down if user demand is greater than initially planned. CryptoKitties, for example, was not very scalable because it was based on Ethereum. This became a source of major issues.
- The costs of achieving infinite scalability primarily regard security. Almost all of the security risks mentioned above become greater with a network of massive scale. In addition, rapidly growing networks require a fast consensus mechanism, in order to validate more transactions while delivering the same speed to individual users. This can only occur in PoS or DPoS. This compromises decentralization. If the protocol is PoW, the hash puzzles or mining algorithms would need to be easier, in order to have a commensurately fast validation process. This compromises security, and to an extent, decentralization.
The Holy Grail of Blockchain
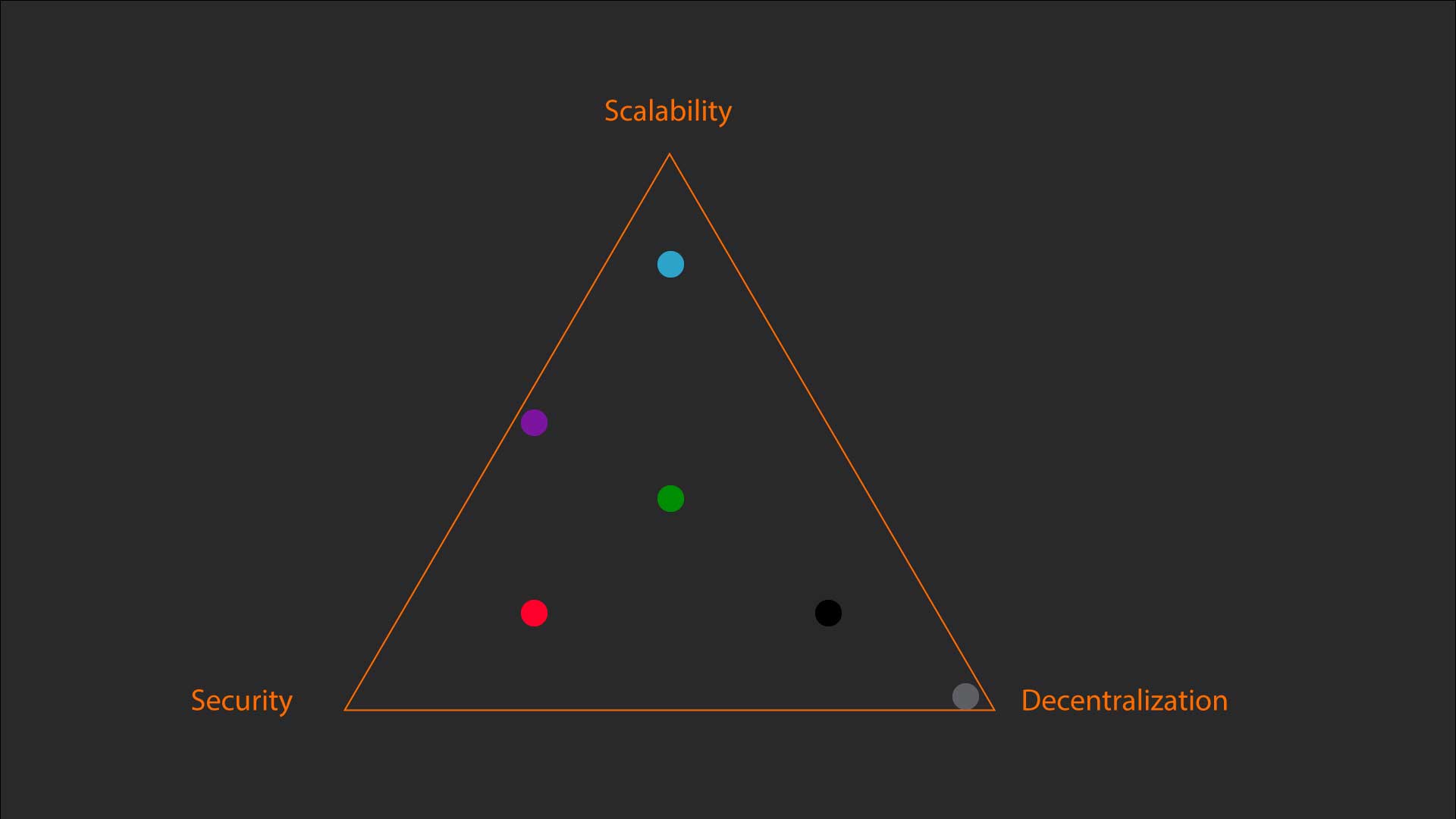
The Trilemma claims that blockchain systems can have at most only two of the following three properties:
Decentralization is defined as the system being able to run in a scenario where each participant only has access to O(c) resources, i.e. a regular laptop or small VPS.
Scalability is defined as being able to process O(n) > O(c) transactions.
Security is defined as being secure against attackers with up to O(n) resources.
Green: The balanced state of all the three conditions.
Red: Robust Security, but limited decentralization and scalability.
Blue: Highly efficient, but with limited decentralization and safety.
Black: Highly decentralized without some essential aspects of security and scalability.
Grey: Decentralized with security and scalability qualities being minimal or absent.
Purple: No decentralization, and a balanced state of security and scalability.
The Holy Grail of Blockchain is finding a solution that combines all three aspects.
Current crypto projects strive to gain the major qualities of decentralization and safety, missing out on scalability opportunities.
Trilemma Solution Options
Alternative ways:
Proof of Stake (PoS)
Proof of Stake (PoS) – allows for potential improvement of scalability. POS replaces cryptocurrency mining, based on the Proof of Work (PoW) system. Validator choice occurs quite quickly, thanks to the determined method, with no power costs.
Sidechains
Ethereum Virtual Machine (EVM) enables the creation of a sidechain to allow a project to handle its particular transactions, and then record only the starting and ending results into the Ethereum network. This reduces pressure on EVM, but gives management opportunities to the sidechain. Trust to third parties decrease decentralization.
Sharding
Sharding breaks up transactions into smaller data fragments. Nodes are separated into groups which handle particular data pieces. Later, these data fragments get assimilated again for constant storage in the blockchain.
Block Size Increase As a Trilemma Solution
Litecoin and Bitcoin Cash (BCH) are forks for the Bitcoin-Blockchain. Generally, forking copies a single blockchain. Both LTC and BCH increased the size of each block, which helped them to store more transactions within the block, and to increase the speed of transactions handling.
Several blockchains working together is a theory that considers scalability. However, there are many issues concerning safety and decentralization. Who owns/manages multiple blockchains? How do they work together?
The most popular option is to create sidechains. Developers have come up with numerous frameworks and solutions.
Lightning Network As a Trilemma Solution
Lightning was the first solution for the sidechain. The underlying concept of the Lightning Network is the idea of not recording all of the transactions into the blockchain, as it overloads the network.
Let’s say users transfer funds to each other several times. In such a case, you do not need to register each transfer. Creating a separate payment channel and recording its data into the blockchain will be enough. This channel can then be opened for as long as needed.
Once a user decides to shut down the channel, all the results of executed transactions will be recorded into the blockchain. Using this suggestion, an entire network of payment channels can be created, and the transactions in the blockchain will be used much less often.
For example, there are three people: P1, P2, P3. Separate channels for payments are opened between P1 and P2, and between P2 and P3. In this way, P1 can send funds to P3 only though P2. This means that P2 will transfer funds to P3, and P1 will compensate expenses to P2.
Blockchain is not really used in this way, and transaction speed is much faster. However, all major operations are done within payment channels.
We can think of payment channels as a safe in which two participants store funds of equal amounts, locking it using two different locks. The amount of funds is recorded into the blockchain, and is called the opening transaction. Immediately, the payment channel is considered to be open. The key idea is that none of the network participants can spend funds independently. Each participant must receive approval from the counterparty. Funds transferred via transactions between only two participants must also be approved.
Imagine that P1 and P2 have established deposits of 5 BTC each. P1 wants to send 1 BTC to P2. To do that, P1 just transfers the right to own 1 BTC from their mutual safe. If they open the safe afterwards, P1 can take only 4 BTC, and P2 can take 6 BTC. However, the safe will not be open until they plan to transfer funds to each other. If P2 sends 2 BTC back to P1 the next day, the same operation of transferring the rights to token ownership takes place. If they open the safe afterwards, the balance of P1’s account will contain 6 BTC, and P2’s balance will be 4 BTC
It should be clear now that a payment channel is just a set of multiple transactions. The channel can be closed by any participant. This action will be some kind of safe opening that allows users to take their funds and record the transfer-related data into the blockchain.
This technology looks impressive when several channels are combined into a network, called the Lightning Network. This network was built specifically for Bitcoin.
Raiden network
The most popular lightning analogue for Ethereum is the Raiden network.
This is an off-chain scaling solution that works with any ERC20 compatible token. Its basic architecture is complicated, but collaboration with Raiden only requires developers to interoperate with API for scalable application creation.
Raiden is meant to ensure instant payments and increase privacy for transactions, micropayments, and low commissions. The majority of payment channels exist outside the chain, and only occasionally form transactions inside the root network, which significantly reduces the root network capacity
Three Raiden projects:
- μRaiden
- Raiden Network
- Raidos
µRaiden (Micro Raiden) is a functioning project on Ethereum. µRaiden is developed with the “one to many” payment option, which allows it to be a payment channel between many users and one decentralized application.
In comparison with other multi-directional transfers available in Raiden, µRaiden is created only for single-direction payment channels.
Raiden Network is Raiden’s main version, currently under testing. The Raiden Network team comprehends the difficulties involved in such a project, and its criticisms. Before launch, their specialists need to make sure they can solve technology-related issues such as:
- Routing efficiency,
- Liquidity issues,
- Absence of support for large payments,
- Potential centralization.
The red eye release for the Raiden Network is expected in the near future, meanwhile the Raiden Echo Node is already available.
Raidos is a side-chain technology for generalized state channels. Generalized state channels can be used to implement random finite automatons, which allow Ethereum’s computational capabilities to scale through the satellite chains. This concept is still under careful examination and planning. It has completed sharding, and is likely to be available in the very near future.
The Solution
Lightning ideologists have gone even further and created a brand new conception of childchains, which solves the blockchain’s speed issues.
Opporty is currently working on Plasma and Plasma Cash concepts.
Plasma is a variety of smart contracts, which are executed on top of the Ethereum root chain and consist of the «child chain» networks, combined by a root chain in the hierarchic tree architecture. The ideologist of Plasma is Joseph Poon, the creator of Lightning for Bitcoin.
Plasma Conception
Plasma Conception is about root chains handling a small number of commits from the child chains so that the root chain is the safest and final storage layer for all intermediate states. Each child chain functions as a separate blockchain with its own consensus algorithm. However, there are some important warnings:
- Smart contracts are created in the root chain and act as an anchor for child chains.
- A created child chain functions as a separate blockchain with its own consensus (usually PoS, not PoW.) All states within the child chain are protected by fraud proofs, which guarantee that all transitions between states are explicit and execute the protocol of withdrawal.
- Specific smart contracts for dapp or child-chain (application logic) can later be deployed into a child chain.
- Required funds can be transferred from the root chain into the child chain.
Validators have economic incentives for acting fairly, and they send commitments into the root chain, the layer of final transaction settlement.
As a result, dapp users who operate in the child chain do not have to cooperate with the root-chain at all. Moreover, they can withdraw all the funds to the root chain whenever they wish, even if the child chain is hacked. These exits from the child-chain allow users to store their funds securely with the help of Merkle proofs, which approve the proprietary rights on a certain amount of funds.
The major advantages of Plasma surround its capability to simplify calculations which currently overload the root chain. Ethereum blockchains can handle wider and more parallel data arrays. Time taken from the root chain also goes to the Ethereum nodes, which have low requirements for handling and storage.
Plasma Cash is a construction that assigns unique serial numbers to in-network tokens that turn tokens into coins. Its advantages include the absence of a need for approval, simpler support for various token types (including NFT), and easement against massive exits from the child chains.
Problems concerning Plasma center around the concept of massive exits from the child chains. In such a scenario, a simultaneous and cooperative exit from a child chain can potentially lead to a lack of compute capacity for withdrawal of all funds. As a result, all the users can lose their funds.
Basic Plasma has ample options for realization.
The major differences are:
- Storing information regarding the storage option and state presentation.
- Token types.
- Transaction security.
- Consensus algorithm types, etc..
Major Plasma variations:
- UTXO based – each transaction consists of entrances and exits: a transaction can be conducted and sent. The list of unspent transactions is the state of the child-chain.
- Account based – contains the reflection of each account and its balance. This type is used in Ethereum, as each account can be of two types: user account and smart contract account. The major advantage of such a storage option is its simplicity. The disadvantage is that this option is unscalable.
Scalable UTXO Plasma chains are divided into four large branches: Plasma MVP, Plasma Cash, Plasma Debit and Plasma Prime.
Plasma MVP
Plasma MVP is a construction for an extremely simple plasma chain, based on UTXO. Core specifications for Plasma MVP allow for payment transactions with high capacity, but do not support more complicated constructions such as scenarios or smart contracts.
One of the blockchain scalability options is the creation of new blockchains. If the number of blockchains that can handle transactions increases, we can increase the general number of transactions to be handled as well. However, creating a new blockchain each time we reach the limit of transactions to be handled per time unit is not a good idea. Independent blockchains simultaneously reduce the general ecosystem’s security and lead to poor user experience.
Sidechain implementation presents an alternative that allows for the creation of side chains, in which funds are tied to the root blockchain. As with the majority of blockchain systems, these side chains require their own consensus mechanism for defining the set and order of the following blocks. If this consensus mechanism cannot work or handle the job, users’ funds can become subject to theft.
Consensus in the Plasma MVP
Blockchains typically need a consensus mechanism. Plasma chains belong to a special type of sidechain that can guarantee security for users’ funds, even if the consensus mechanism in Plasma fails to perform. As a result, the simplest MVP version relies on an operator. An operator is a unit that effectively manages the entire Plasma chain, creating blocks. This means that MVP utilizes Proof-of-Authority consensus.
PoA can seem vulnerable, even if the operator acts in a fair way. This key feature also allows for the use of Plasma MVP for private blockchains, guaranteeing that users can maintain control of their cryptocurrencies.
Users have begun to utilize the Plasma chain, depositing funds into smart contracts on Ethereum. Basic specification MVP allows users to deposit only ETH, but the specification can be easily expanded to support ERC-20. When users deposit their funds, a special block is created in the Plasma chain that holds only this one transaction. The transaction creates a new output for the contributor, equal to the cost of the sums deposited in accounts. As soon as users make deposits, they are ready to create transactions in the Plasma Chain.
Users can conduct their own deals, spending their own outputs and creating new ones. Each transaction and its corresponding signature then go to the operator.
The operator receives a variety of transactions and includes them in a sorted list of transactions, called a block. As soon as the operator receives enough transactions to fulfill a block, a сommitment is sent to Ethereum. To explain exactly how the commitment works, we first need to define the Merkle tree.
Merkle Trees And Their Role in Plasma
Merkle trees are extremely important in the Blockchain world. Merkle trees enable us to record a certain array of data in a way that hides the data, but allows users to prove that part of the information was in the array. For example, if we have ten numbers, we can create a commitment for them, and then prove that one particular number exists in that set. These commitments have a small constant size, which makes them inexpensive to convert to Ethereum.
We can use this feature for a given set of transactions, and we can even prove that a certain transaction is in the set. This is what the operator does. Each block consists of a set of transactions that become the Merkle tree. The roots of this tree provide proof that is submitted to Ethereum with every Plasma block.
Users must have the ability to withdraw their funds from the Plasma chain. When users wish to leave the Plasma chain, they send an “exit” transaction to Ethereum.
Exit From Plasma and Types of Exits
Funds in MVP are represented as UTXO, therefore each exit has to point to a certain exit. Only the product owner can call it off. For this reason, the user has to present Merkle Proof, together with the exit, to start the funds withdrawal. A smart contract checks the proof to make sure the transaction that created the output data was included in a certain block. The contract also checks whether the output data belongs to the user who started the exit.
We also want to make sure that a link to the results is unexpended. To do so, we add the call interval. Basically, a call interval is a period of time for users to dispute the validity of an exit and prove that UTXO is expended. Users can prove that UTXO is being spent, unveiling other transaction that spend UTXO, signed by the user who started the exit.
The exit protocol allows people to withdraw their funds from the Plasma chain. Unfortunately, the Plasma operator is allowed to make wrongful actions, such as transactions with double expenses, and there is nothing we can do to stop them. The operator can also make an exit from an exit created by an invalid transaction.
This problem can be solved in the following way: First, the UTXO has the “exit priority,” depending on whether they were included in the plasma chain. The exit priority is based on the UTXO “location” in the block, and on the output’s index in the transaction, which provides us with a unique position for each UTXO.
Meanwhile, “old” UTXOs are deleted earlier than newer ones.
What happens if a transaction is added right after an unsuccessful one? It can happen, if the user executes a transaction; the transaction goes to the operator, and the operator puts the invalid transaction before the valid transaction from the user. Users can try to exit the entry data, but this exit can be challenged by defining the signed expenses.
Transfer Approval and Dual Signature
The solution here is to keep making transactions invalid until they have been signed twice. Each time a user executes a transaction, the first signature causes the transaction to be added to a block. Once the transaction is added to a valid block, the user adds a second signature, called an approval signature. Users who obey the rules will never add an approval signature unless they are sure that their transactions were added to valid blocks.
When making an exit, an approval signature is also required. Now, if the operator includes a user’s transaction after an invalid transaction, the user will not sign it. A transaction added after an invalid transaction will have no signature, and therefore will also be invalid. This ensures that only honest users can get their funds back.
An NFT is a non fundable token. Users cannot divide this token. It belongs to the ERC 721 standard.
NFT tokens can be used to remove the dual signature and to increase scalability, because each block can contain only one expense. We can track the entire chain, and the operator can appear to be false. This issue can be solved by Plasma Cash.
Plasma Debit Variation
Plasma Debit is the same as Plasma Cash, but each token becomes a payment channel between a user and the operator. All payment channels can be sent in the same way as with Plasma Cash. Deposits and withdrawals using Plasma Debit are the same as with Plasma Cash, but transactions differ in the usage of payment channels.
Each time a user wants to make payments in tokens, special payment channels created to send tokens to other users are re-used, and payment is made to the operator, who transfers the funds to another user.
The recipient must also have an open channel with the operator who receives the sent funds.
If the recipient has no channel or an operator has no blocked funds, then Plasma Debit cannot guarantee that the token will be sent
Plasma Debit utilizes the advantages of Plasma Cash. Payment channels in Plasma Debit are tokens, as with Plasma Cash, and they can be sent to other users.
Tokens as Payment Channels in Plasma Debit
In this example, user A wants to send 1 ETH to user B, but he is not yet a part of the network. User B has not yet created a channel, and the funds cannot be sent, because funds transfer is a job for the operator. We can think of an automatic way for channel creation, but this solution is not ideal.
Now, when users A and B have all the necessary channels, they can start sending payments through the channels. These payments are instant, secure and easy to execute.
In short, the operator serves to ensure proper liquidity and to submit blocks to the root chain.
Each account has its own amount that can be withdrawn, and the amount put on the deposit. If we sum up the amounts of all the accounts in the Merkle tree transactions, we will receive a total sum of the liquidity, inputted by the operator into the network.
To receive a transaction in 5 ETH after connecting to the network with 10 ETH in the deposit account, we have to take one of the following actions:
Send 5 ETH to anyone who has a difference in ≥ 5 between the sum of input and output; or, ask the operator to provide liquidity and increase the output sum to 15.
The disadvantages of Plasma Debit are that the operator is always centralized, and it is impossible to implement a consensus algorithm into Plasma Debit.
Plasma Prime Variation
Another iteration of Plasma is called Plasma Prime, which uses RSA accumulators to short-cut the size of history by several times.
This solution is based on the UTXO model, where each unexpended output defines the ownership of a certain segment. The segment length is equal to the token price that was added to Plasma.
Each segment is shown as a prime number, generated by a simple hash function.
Because of the limitations of generated prime numbers, Plasma has a final set of segments that can be owned by different owners during the Plasma life cycle.
Let’s take the X segment for example. During time A, a certain transaction was created. This transaction had an impact on X; for example, it caused transactions to split or merge.
During time B, other transactions were submitted.
When the transaction C is submitted, we need to check whether the history of this transaction is valid.
Therefore, we need to generate a proof that grasps only those transactions related to the X range, not to the entire transaction history.
RSA Accumulators For History Compression
RSA accumulators are used for history compression. An RSA accumulator is a data structure that ensures functionality, similar to the Merkle tree. A massive amount of data can be compressed into one “root” of a fixed size in a way that, considering the data and the root, we can create “evidence” for proof.
For example, we pick the number N. Its factorization is unknown, and the ‘g’ generator (let’s say g=3) is an empty accumulator. To add ‘v’ into accumulator A, we implement a new accumulator A2=Av. To prove that ‘v’ is a part of accumulator A, we use a proof of knowledge of the coefficient in the exponential scheme, proving that there is a cofactor ‘x’ such that (gv)x =A (x can be a large number.)
In this way, we can significantly reduce the history size in Plasma Prime.
Plasma Cash: Opporty’s Solution
Opporty utilizes its first realization of Plasma Cash Protocol.
Plasma Cash Protocol is the most efficient Plasma implementation when it comes to scalability.
Plasma Cash is a construction, based on utilizing unique identifiers for each token in the Plasma chain. In other words, we use NFT tokens that are assigned unique serial numbers.
Sharded validation on the client side: Clients must track their Plasma chains to receive tokens, which means that a transaction’s capacity can be increased without increasing the burden on other users.
Reducing the risk of mass exit: Mass exits are less threatening to the network, because an exit transaction must be presented for each token withdrawn, reducing the risk of theft.
There is no two-way authentication, and transactions no longer require two-phase sending and approval. Instead, once a transaction is included in the main chain, it can be spent.
A disadvantage is the large nominal of tokens. Each token has a serial number, so there is no way to randomly create small tokens. This is due to the fact that the token price will be higher than the initial price at some point.
Transactions Structure in Opporty’s Plasma Cash
Each transaction in Opporty Plasma Cash is:
[[prev_hash, prev_block, token_id, new_owner], signature]
The key point here is that there is a link to the previous block (so you can move in chain order, one by one), and the token identifier has to be unique. Also, there is a signature based on the BLS algorithm.
To create a block and receive a root hash, we use a special Patricia Merkle Tree. It is shown in its concise form, but we can still receive proofs of transactions being included in blocks or excluded from them.
A transaction that spends a token with the token_id data is valid only if included in the Merkle tree of the token_id position; this means that each token on the Merkle tree has its own “place” where transactions that spend tokens can be executed. This allows users to check their Plasma chain’s history, and prove or deny ownership for their particular tokens. It can also be optimized with the help of the RSA accumulators, as we described earlier.
In order to spend tokens, we have to validate the chain first and check it for the absence of missed blocks. Only after that can we re-sign the transaction, along with the entire history.
Output Options in Plasma Cash
Anyone can withdraw tokens by presenting the latest two transactions in the history of token ownership.
The output can be disputed in three ways:
- Showing confirmation of the transaction expenses.
- Showing confirmation of the previous transaction expenses.
- Showing the transaction in the token’s history.
Calling the first or second option leads to an immediate exit block. Calling the third option, we can provide a linear descendant, C *, which must be equal to or less than P (С).
In addition to Plasma Cash being an incredibly reliable tool, it also allows for the realization of consensus algorithms that provide an excellent opportunity to enhance the network’s security and credibility.
Results/Achievements
Having a PoA sidechain based on the Ethereum platform increases our chances of accelerating transaction speeds dramatically.
Opporty has achieved up to 300,000 transactions per second on a single operator, a much larger number than other current payment systems can handle.
Despite some minor issues with data availability, the operator ensures a high level of Blockchain stability and enables fast and efficient performance of international business transactions.
Plasma Cash makes an enormous impact on scalability, which is why Opporty utilizes Plasma as part of its PoE protocol.